In this episode of Intrusions in Depth, host Josh Stepp explores the intriguing theory that Phineas Fisher may be linked to Russian intelligence. Inspired by a listener's email and drawing on various data points and historical incidents, Josh delves into the possibility of Phineas Fisher being a Russian asset, comparing their tactics to those of known cybercriminals and government operatives.
Main Topics:
1. History of Cyber Operations and Notable Cases
Examination of various APT (Advanced Persistent Threat) groups and their activities, including Fancy Bear (APT 28) and the Lazarus Group.
Discussion on how cybercriminals often evade capture due to operating out of countries that do not cooperate with international law enforcement.
2. Chaos Agent: Maksym Igor Popov
Detailed account of Popov's activities, including his dual role as an informant and a hacker.
Comparisons between Popov's tactics and those of Phineas Fisher, highlighting the use of disinformation and false flag operations.
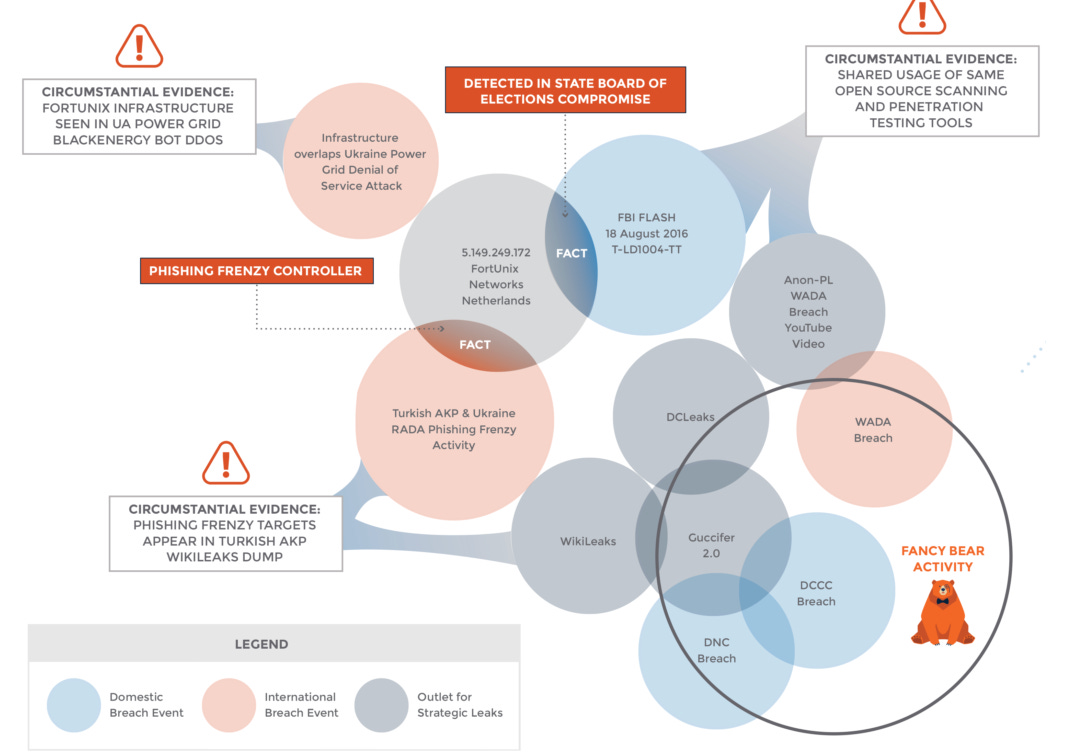
3. Analysis of the AKP Attack and WikiLeaks Involvement
Examination of the AKP email dump and its timing with the Turkish coup attempt.
Discussion on the use of a specific IP address linked to Russian cyber activities and its implications for the theory.
4. Potential Connections and Speculative Points
Analysis of various indicators that could suggest a link between Phineas Fisher and Russian interests.
Consideration of the broader geopolitical context and the use of hacking as a tool for political influence.
Call to Action:
Subscribe to the podcast for more episodes on high-profile cyber intrusions.
Visit our website at intrusionsindepth.com for additional stories and insights.
Share your thoughts on social media using #IntrusionsInDepth.
Links and Resources:
https://nkwt.blogspot.com/p/informazioni.html
https://www.vice.com/en/article/what-went-wrong-with-the-turkey-data-dump/
https://emma.best/2019/03/20/the-russian-contractor-who-infiltrated-anonymous/
https://www.techtarget.com/searchsecurity/news/252518151/Iranian-APT-Cobalt-Illusion-launching-ransomware-attacks
https://www.bankinfosecurity.com/isoon-leak-shows-links-to-chinese-apt-groups-a-24713
https://en.wikipedia.org/wiki/Jeremy_Hammond
https://www.darknet.org.uk/2016/04/phishing-frenzy-e-mail-phishing-framework/
https://www.history.com/news/whitey-bulger-fbi-informant
https://archive.is/REs0G
https://web.archive.org/web/20160418221027/https://twitter.com/gammagrouppr
https://archive.org/details/MaksymIgorPopov/POPOV%2C+Maksym+Igor/HILBERT/popov-flashes-cash.mp4
https://www.wired.com/2016/05/maksym-igor-popov-fbi/
https://emma.best/2018/11/15/sealed-files-allege-assange-and-wikileaks-solicited-hacks-against-governments-politicians-and-corporations/
https://steemit.com/politics/@tvorhet/why-has-nobody-questioned-the-provenance-of-phineas-fisher
https://threatconnect.com/resource/webinar-guccifer-2-0-the-dnc-hack-and-fancy-bears-oh-my/
https://medium.com/@securityaffairs/evidence-on-hacks-of-the-us-state-election-systems-suggest-russian-origin-682e4f016e0e
https://securityaffairs.com/50754/uncategorized/state-election-systems-hacked.html
https://latesthackingnews.com/2016/09/06/us-state-election-system-hacks-connected-ukraine-power-grid-attacks/
https://news.softpedia.com/news/us-state-election-system-hacks-connected-to-ukraine-power-grid-attacks-508011.shtml
https://securityaffairs.com/49575/hacktivism/phineas-fisher-erdogan-emails.html
ThreatConnect Image of connections:
Credits:
Host: Josh Stepp
Produced by: Josh Stepp
Thank you for tuning in to Intrusions in Depth. Stay informed, stay safe, and see you in the next episode!













Share this post